16 February 2026 · articles
Technical deep dive: SD-WAN, ZTNA, and proxy technologies
Technical guide to SD-WAN, ZTNA, and proxy technologies. Learn how these three solutions integrate to create secure, scalable network architectures.
16 February 2026
Author: Ben Rees, Senior Network Product Engineer | Estimated Read Time: 6 minutes
Enterprise networks face three challenges: connecting distributed sites efficiently, securing application access without exposing networks, and protecting users from web threats. SD-WAN, ZTNA (zero trust network access), and proxy technologies solve these problems by working as an integrated system.
What is SD-WAN and why do organisations use it?
SD-WAN (Software-Defined Wide Area Network) connects distributed sites and branch offices using intelligent software rather than expensive MPLS circuits. The technology routes traffic across any available transport including broadband, 4G/5G, and dedicated internet access.
How SD-WAN makes routing decisions
The system classifies traffic by application using deep packet inspection. Each data flow routes based on:
Application requirements (latency sensitivity, bandwidth needs)
Link quality metrics (jitter, packet loss, availability)
Security policies (encryption requirements, approved paths)
Real-time performance monitoring
If a link degrades or fails, traffic automatically shifts to alternative paths without disrupting active sessions.
Business benefits of SD-WAN deployment
Organisations choosing SD-WAN report several measurable improvements:
Sites go live in days using readily available internet circuits
WAN costs decrease 30-50% by replacing or supplementing MPLS
Application performance improves through intelligent path selection
Configuration happens centrally with changes deployed in minutes
Teams gain real-time visibility into performance across all locations
The technology also includes integrated security features such as IPsec encryption, firewall capabilities, and direct cloud access for SaaS applications like Microsoft 365. For a complete overview of how SD-WAN transforms network infrastructure, see our comprehensive SD-WAN guide.
How does ZTNA differ from traditional VPN?
Zero trust network access provides secure application access without exposing your network. Traditional VPNs grant broad network access once authenticated. ZTNA grants access to specific applications only, making the network infrastructure invisible.
The ZTNA authentication and access process
When users attempt to access an application, this sequence occurs:
User authenticates against your identity provider (Azure AD, Okta)
ZTNA controller evaluates user role, device compliance, location, time
System checks all conditions against defined security policies
If approved, a micro-tunnel connects user directly to that specific application
Network remains hidden; users cannot discover other applications without permission
Key differences between ZTNA and VPN
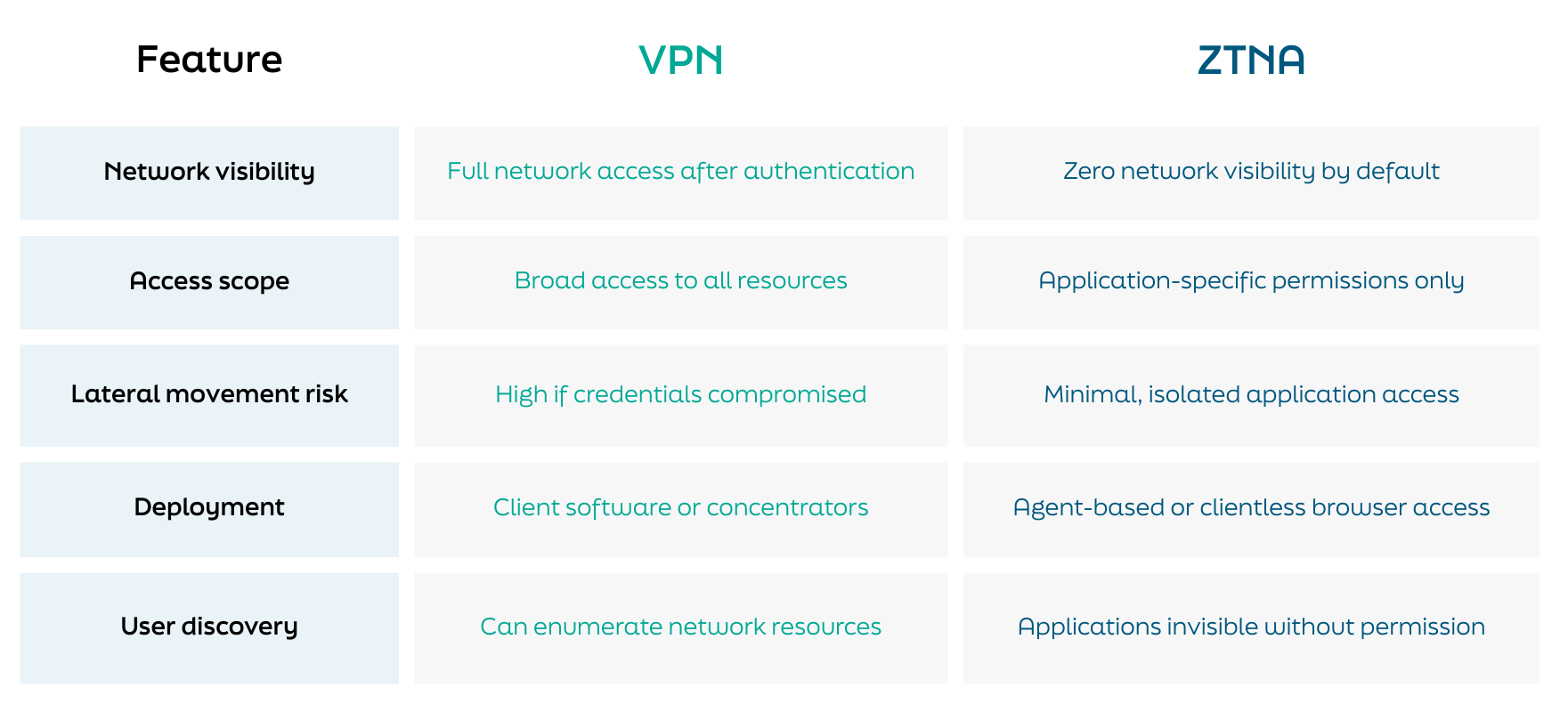 Modern ZTNA platforms integrate with existing identity systems, evaluate device posture continuously, and provide detailed audit logs of all access attempts. To understand how zero trust principles extend beyond ZTNA into complete architectural frameworks, read our zero trust architecture guide.
Modern ZTNA platforms integrate with existing identity systems, evaluate device posture continuously, and provide detailed audit logs of all access attempts. To understand how zero trust principles extend beyond ZTNA into complete architectural frameworks, read our zero trust architecture guide.
What do proxy technologies do in network security?
Proxy technologies sit between users and the internet, inspecting traffic to enforce security policies and block threats. Web proxies act as intermediaries for HTTP and HTTPS traffic, evaluating every request against security rules before forwarding approved traffic.
Security functions enabled by proxy inspection
Proxies provide critical security capabilities:
Enhanced URL filtering against threat intelligence feeds and malicious sites
Content scanning for malware before reaching user devices
Data loss prevention by inspecting outbound traffic for sensitive information
Acceptable use policy enforcement for inappropriate content
Complete activity logging for compliance and forensic investigation
Secure Web Gateway vs traditional proxy
Secure Web Gateways (SWG) operate from distributed cloud locations rather than on-premises appliances. Users connect to the nearest cloud point of presence, which enforces security policies before allowing internet access. This cloud-delivered model ensures consistent protection regardless of user location.
Typical enterprise traffic flow
Consider a branch office user accessing different resources:
Internal application access: SD-WAN routes traffic to cloud security stack → ZTNA verifies identity and device compliance → secure connection established to specific application
Internet browsing: SD-WAN recognises web traffic → routes through proxy services → content inspected and policies enforced → approved traffic forwarded
SaaS applications: SD-WAN provides direct internet breakout → proxy inspects traffic → optimised path to cloud service
All coordination happens automatically in milliseconds.
Integration benefits across the stack
The unified approach delivers several operational advantages:
Security policies remain consistent regardless of user location or connection method
ZTNA gains context from device posture tags and policy
Proxy inspection can trigger additional authentication if suspicious patterns detected
Integrated control plane and centralised management planes
New sites and users added through centralised management without complexity
What are the deployment considerations for hybrid environments?
Moving from planning to implementation requires decisions around network topology, cloud integration, and policy design.
Network topology options
Three primary architectures suit different requirements:
Hub-and-spoke: All traffic routes through central data centres providing strong security controls but potential bottlenecks
Full mesh: Direct site-to-site connectivity improves performance but increases management complexity
Hybrid design: Security-sensitive traffic flows through centralised inspection while direct connectivity optimises routine application access
Cloud-first infrastructure requirements
Cloud-first environments need specific architectural choices:
Direct internet breakout from branches for SaaS applications requires cloud-delivered security services
Private connectivity to AWS and Azure for workloads requiring consistent latency or compliance
Cloud-delivered security with points of presence near users for optimal performance
Integration between SD-WAN edge devices and cloud security inspection services
Policy design in layers
Effective policies separate concerns for clarity and maintainability:
Network policies: Define which sites can reach which resources
Security policies: Specify inspection and controls for different traffic types
ZTNA policies: Determine who can use applications under what conditions
Telemetry and logging: Enforced regulatory and compliance requirements for logging and data handling.
This separation makes policies easier to modify and troubleshoot.
Financial services security and compliance
Banks and financial institutions require stringent security with regulatory compliance. A regional bank replaced MPLS circuits with SD-WAN, reducing WAN costs 40% while maintaining quality of service. ZTNA provided secure access to customer account systems for mobile bankers, eliminating VPN performance issues. Proxy technologies inspect all web traffic with SSL inspection configured to meet monitoring requirements without compromising customer privacy.
Manufacturing operational technology protection
Manufacturers with distributed facilities need secure connectivity for production systems. A European manufacturer deployed SD-WAN connecting production sites, warehouses, and logistics centres. ZTNA allows suppliers and logistics partners to access specific systems without VPN access to the entire network. Proxy services protect industrial control systems from internet threats while allowing necessary updates and remote monitoring.
Professional services client data security
Consulting firms require secure access to client systems from any location. A firm implemented ZTNA providing consultants with access to client project systems based on specific engagement assignments. SD-WAN ensures consistent connectivity between offices and cloud-based practice management tools. Proxy technologies enforce acceptable use policies with detailed logging supporting client confidentiality requirements.
Retail point of sale reliability
Retail chains need reliable connectivity supporting transactions and inventory management. A retailer used SD-WAN to connect hundreds of stores with broadband and 4G connections, eliminating MPLS dependency. ZTNA provides regional managers with secure access to store systems. Proxy technologies protect store networks from malware and enforce content filtering on shared devices. The solution handles peak transaction volumes during busy periods while maintaining security.
How do you migrate from legacy infrastructure?
Successful migration from traditional VPN and MPLS infrastructure requires phased implementation that minimises risk while building team capability.
Recommended migration phases
Pilot programme: Validate technology choices with 2-3 non-critical sites
Operational validation: Test monitoring, troubleshooting, and change management procedures
Gradual rollout: Deploy to additional sites in waves based on complexity and criticality
Parallel operation: Run old and new systems simultaneously during transition
Legacy decommission: Remove old infrastructure once new platform proves stable
Performance expectations to set
Realistic expectations prevent dissatisfaction:
TLS inspection adds 5-20 milliseconds of latency depending on implementation
ZTNA authentication occurs per session but requires identity system availability
SD-WAN path selection responds to conditions but cannot overcome circuit limitations
Initial device provisioning takes minutes but policy changes deploy instantly
Team readiness requirements
Operational capability determines long-term success:
Training on new platforms and integrated architecture thinking
Runbooks documenting common scenarios and troubleshooting steps
Monitoring spanning all layers to catch issues before user impact
Change management accounting for interdependencies between components
What does unified secure access architecture deliver?
Networking and security converge into integrated platforms. SD-WAN transforms WAN from a constraint into an enabler through intelligent routing. ZTNA replaces perimeter security with application-specific access control. Proxy technologies provide the inspection layer for detecting threats.
This convergence defines the SASE (Secure Access Service Edge) model, where networking and security capabilities combine into a single cloud-delivered service. Platform thinking beats point solutions. Your SD-WAN, ZTNA, and proxy technologies should work as a coordinated system, sharing context and enforcing consistent policies. The control plane provides unified visibility. Deployment happens in days through automation.
For organisations navigating hybrid cloud, supporting distributed workforces, or modernising legacy infrastructure, these technologies provide the foundation. Separate tools converge into integrated SASE platforms that simplify operations while improving security. Network and security teams work from a shared view. Users get seamless access without navigating multiple steps or accepting performance compromises.
The goal is connecting users and applications securely, efficiently, and at scale. SD-WAN, ZTNA, and proxy technologies, integrated within a SASE framework, deliver that outcome.
Learn more about Cloud Gateway
Cloud Gateway is reimagining the enterprise network, challenging outdated models and setting a new standard for how technology should operate. We believe connectivity and security should be agile, visible, and under your control.

/f/148396/1875x1250/f831b61f36/network-architecture-cgw-header.png)